Step by Step guide to SSO Setup with LDAP Authentication
This article is designed to configure LDAP with OvalEdge. In order to authenticate your users against Windows, you need to feed some properties to the OvalEdge application.
Required Properties
To configure Your LDAP with the OvalEdge application, the properties you need are:
- LDAP URL
- Port number
- ldap.rootDn
- ldap.managerDn
- ldap.managerPassword
- ldap.userSearchFilter
- ldap.userSearchBase
- ldap.groupSearchBase
- ldap.groupSearchFilter
After collecting the properties, please follow the below steps carefully to set up SSO with LDAP Authentication.
Any kind of discrepancies in configuration file may hinder the application execution.
Steps to Configure LDAP Authentication
- Please update the LDAP information in oasis.properties, values in bold must be updated.
ldap.customRolePrefix=com.ovaledge.
ldap.userSearchFilter=(&(objectClass=inetOrgPerson)(SAMAccountName={0}))
ldap.userSearchBase=CN=Users,DC=ovaledge,DC=net
ldap.groupRoleAttribute=
ldap.groupSearchFilter=(&(objectClass=groupOfNames)(member={0}))
ldap.groupSearchBase=CN=OE_ADMIN,CN=Users,DC=ovaledge,DC=net
ldap.url=ldap://localhost:389
ldap.managerDn=CN=admin,CN=Users,DC=ovaledge,DC=net
ldap.managerPassword=0valEdge!
ldap.rootDn=DC=ovaledge,DC=net
ldap.usermapping.firstName=givenName
ldap.usermapping.lastName=sn
ldap.usermapping.email=mail
ldap.roles.source=ldap
After updating the details in the oasis.properties, the file will be displayed as below:
- LDAP users must have one of the OvalEdge Roles to get the authorization to data objects in OvalEdge.
- Let’s say OE_ADMIN, OE_METAREAD, OE_METAWRITE, etc., roles are set up in OvalEdge. If we set up and add any of these roles to a user in LDAP, upon login to the OvalEdge application, the corresponding Roles get automatically assigned to the user.
- If a user login to the OvalEdge application with LDAP credentials and without any Roles, the OE_PUBLIC role will be assigned to the user.
- If the Administrator assigns some role to a user in the OvalEdge application and it is not configured/added to the user in LDAP, it will be removed upon login to the application.
- OvalEdge supports the HYBRID model as well.
- Authentication is handled by LDAP, and OvalEdge takes care of authorization.
- In this case, we don’t need to create or add any Roles to Users in LDAP. It can be handled completely within the OvalEdge.
- The application will only check Authentication and add/ update users based on the information(Username, First Name, Last Name, email ID) received upon login.
- To support Hybrid model, we need to set roles.source as ovaledge, otherwise, keep as ldap.
- Sometimes, LDAP roles will be prefixed by a fixed string by some Administrators.
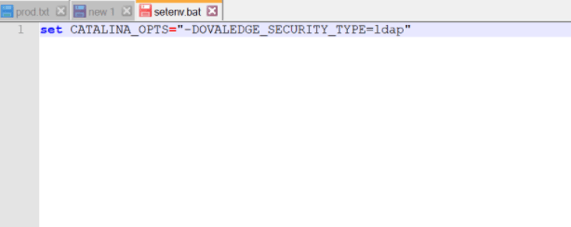
Example: all roles are prefixed with GT_(GT_OE_ADMIN, GT_OE_PUBLIC). In this scenario, we must configure GT_ as Custom Role Prefix (ldap.customRolePrefix). - Add the below entry in VM Arguments (setenv.sh)
-DOVALEDGE_SECURITY_TYPE=ldap
- Start the server, and log in with LDAP Username and Password.
Now you will be connected to the OvalEdge application using LDAP Authentication.
Copyright © 2023, OvalEdge LLC, Peachtree Corners, GA USA