Introduction to OvalEdge Security
Since a data catalog houses information about all the data, it’s critical that there are guardrails protecting the most sensitive files. The objective of this chapter is to make you familiar with various security management strategies and best access management practices for viewing data in OvalEdge.
This chapter introduces the OvalEdge security model and includes the following sections:
Security Model
The OvalEdge Security module allows the Administrator to monitor, maintain security and manage user permissions that are set on data objects. Access to the data and metadata in OvalEdge is controlled using role-based access. Associating a user account with one or more user roles allows Administrators to control each user's access to OvalEdge modules, data objects, and responsibilities.
Role-Based Access Control
Roles are the major part of access control in OvalEdge. Users, metadata permissions, data permissions, and responsibilities all relate to the roles.
A user can have multiple roles.
A role can have different permissions on various data objects.
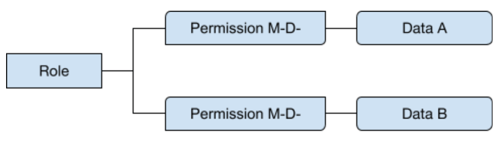
Permissions are used to define the ability to perform certain actions on a data asset. There are two kinds of permissions.
|
Meta Permission |
Description |
|
|
MR |
Metadata – Read |
Users can View the Metadata |
|
MW |
Metadata – Write |
Users can View and Edit the Metadata |
|
Data Permission |
Description |
|
|
DN |
Data – No Access |
A user cannot see the data |
|
DP |
Data – Preview |
A user can see the data but cannot query to download |
|
DR |
Data – Read |
A user can see, query, and download the data |
|
DW |
Data – Write |
A user can see, query, download & write the data to the Database. Write permission has all the possibilities like creating a table, inserting or updating data, etc. |
|
ADM |
Administration |
Admin permission is the highest level permission, this means they can provide access to others. The only exception is data masking. Even ADM can’t see masked data. |
Managing users and roles is a simple task compared to managing roles and data. As data is naturally cataloged technically using its Schema or Reporting Systems, you can organize your data permissions.
For more details on how roles and permissions work in OvalEdge, see Setting up Security using Roles and Permissions article
Component Level Security
The metadata access In OvalEdge can be set up in five levels.
Data Asset Level
Contains managing databases, tables, reports and files, and folder <Setting up Security on Files and Folders>
Application Level
Each module and submodule in the OvalEdge application can be protected by limiting access to certain user roles. For more information, see <Setting up Application Module Security>
OvalEdge Object-Level Security
OvalEdge provides the simplest way to manage and control access to various components of data. See <Objects security > for more information on how to control access.
Column Level Security
In OvalEdge, you can restrict access to certain columns globally or for a specific role. Column level security is mostly used for privacy or confidential data. In an ocean of data, it’s often very difficult to find private or confidential. For more information, see <Column or Field Level Security>
Managing Permissions
Managing Data Permissions via Technical Domain
As data is already grouped with the technical schemas, reporting groups, and other domains, you can easily configure security at this level. By default, OvalEdge can be configured to perform security processes at the schema level.
Managing Data Permissions via Functional Domains
As well as security and responsibilities, you can also manage at the functional level. This is done in OvalEdge via functional tags called Data Asset Groups (DAGs). You can create DAGs and assign security and responsibilities to them. Then, you can assign various schemas and tables to this tag. All security will be maintained via these DAGs.
OvalEdge uses the following techniques to manage data permissions technically and functionally.
- A user can have access to multiple roles while each role can grant access to multiple data objects. In the end, a user will obtain whichever role provides maximum access.
- A role can be assigned to metadata permissions and data permissions.
- Column level security means you can mask or restrict access to specific fields in a table.
- User to role assignments can be easily managed with a company's existing infrastructure like Okta or Active Directory, but role to data mapping management is complex.
- OvalEdge provides multiple tools like DAG (Data Asset Group) to group data functionally, AI algorithms to find PII or any confidential information, and manage security easily.
License Types
OvalEdge Software is licensed to a customer based on a license model with a defined license type, which is used to measure the number of licenses required. Refer to <license model document/contact sales for different license models>. Every license model is defined with three different license types based on
- Total connections
- Users
- Default & Additional features
Each user role created in OvalEdge is associated with a “user-based license” as follows:
Author License- An user role created with an Author license can either have metadata read or write permission. Along with the metadata access, users can be given either Data No access/Data Preview/Data Read/ Data write access.
Reader- An user role created with a Reader license can have only Metadata Read permission. Additionally, Reader users can be given either Data No access/ Data Preview/ Data Read access.
Reader Preview- An user role created with a Reader Preview license can have only Metadata Read permission. Reader preview users can be given either Data No access/ Data Preview access.
|
Security-Manage Roles |
|
|
License Type |
Permissions which we can provide to them |
|
Author |
MRDN, MRDP,MRDR,MRDW, MWDN,MWDP,MWDR,MWDW |
|
Reader |
MRDN, MRDP, MRDR |
|
Reader Preview |
MRDN, MRDP |
The following is the hierarchy of the license type from highest to lowest in OvalEdge Author>>Reader>>Reader Preview.
Administration Glossary
User- An User is one who has a certain level of privileges to access the data assets and objects within an application.
Role- A Role is a set of rights and responsibilities that can be associated with a user or group of users.
Permission- A permission provides a role with the capability to perform certain actions (read, insert, update, delete and etc.) on data objects. Permissions available for a role are controlled by the role license type mapped to it.
Objects- An object is a component of interest that refers to a cluster, host, App Server, or database.
Assets-An asset refers to the group of data such as tables, files, reports, and queries.