AWS Secrets Manager Configuration
This document provides information about fetching the OvalEdge MySQL/MariaDB database and Elasticsearch connectivity details from AWS Secrets Manager.
What is AWS Secrets Manager?
Amazon Web Services (AWS) Secret Manager helps you to securely store and manage passwords, database strings, and API keys. Secrets can be stored, managed, and retrieved conveniently and securely through a central repository.
For more information, please refer to AWS Secret Manager
How to use AWS Secrets Manager to read DB and ES credentials?
In OvalEdge, MySQL/MariaDB is used as a relational database management system to store structured data. ElasticSearch, on the other hand, is used as a search and analytics engine to store and retrieve unstructured or semi-structured data. Together, these two technologies enable OvalEdge to efficiently store, manage, and retrieve both structured and unstructured data.
In order to connect to a MySQL/MariaDB database or ElasticSearch, typically one would require a host, username, password, and other connection parameters. This information will be stored in a file “oasis.properties” and read by the application. If someone gains access to this file, they could potentially connect to the OvalEdge database and ElasticSearch, which may lead to data loss or security vulnerabilities.
To address this concern, OvalEdge can read the Database and ElasticSearch credentials from AWS Secrets Manager as a more secure alternative. With AWS Secrets Manager, secrets can be stored in a key vault and accessed directly when establishing access to the database. This provides greater control over managing secrets and ensuring their protection.
AWS Secrets Configuration in OASIS Properties File
Step 1: Obtain the Key-Value Parameter
- Log into the AWS portal using IAM User authentication.
- Click on Secrets Manager which will display the Secrets names.
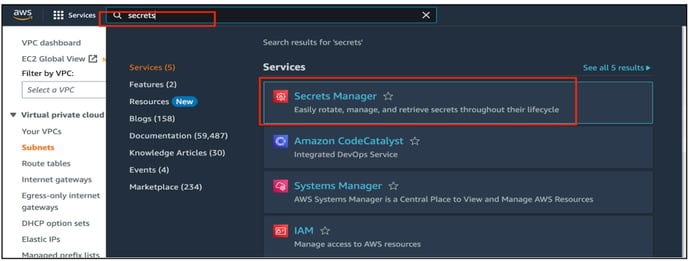
- When you click on Secrets, you will see the Secret Keys and its corresponding values which will be used to configure the OASIS property file.
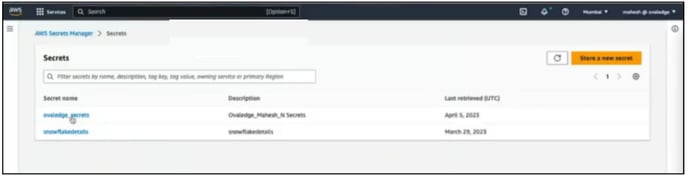
- Next, Click on the Secret Value that will display the list of Key-Value pairs.
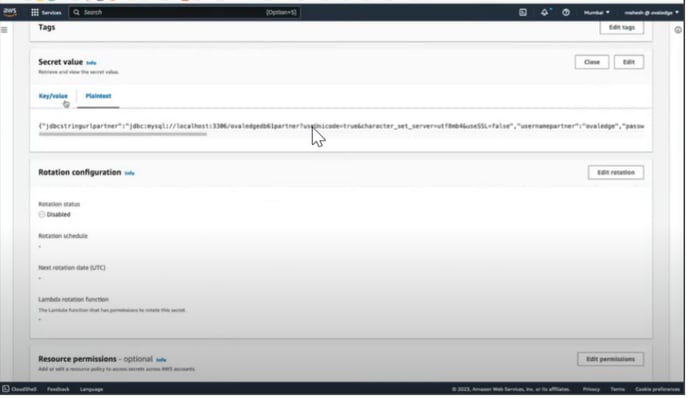
Step 2: Connectivity to AWS Secrets Manager
OvalEdge will use AWS Role based authentication to connect to AWS Secrets Manager. So, we have to create a Role that has access to the AWS Secrets manager and attach this Role to the OvalEdge box (VM)
Step 3: Add the Key-Value parameter in the oasis.properties
Once you have required the Secret Key Value, it can be added to the below parameters.
To use AWS Secrets Manager with OvalEdge, you can provide a parameter called "aws_secrets" with a value of either True or False. If it is True, then OvalEdge will use AWS Secrets Manager to fetch the database credentials. If it is False, then OvalEdge will use the credentials configured in the "oasis.properties".
Following are the fields added for AWS Secrets for Database
aws-secrets=true
aws-secretregion={AWS Region}
aws-secretname={Name of the secret}
secret.key.jdbcstring={secret key for the jdbcstring}
secret.key.username={secret key for the username}
secret.key.password={secret key for the password}
secret.key.read.jdbcstring={secret key for the readjdbcstringurl}
Following are the fields added for AWS Secrets for Elasticsearch
secret.key.esenabled=true
secret.key.eshost={secret key for the eshost}
secret.key.esport={secret key for the esport}
secret.key.esprotocol={secret key for the esprotocol}
secret.key.esusername={secret key for the esusername}
secret.key.espassword={secret key for the espassword}
Copyright © 2023, OvalEdge LLC, Peachtree Corners GA USA